
CYBERSECURITY MANAGED SERVICES
Protect your organization against malicious activity with technology solutions from leading providers purpose-built for your needs.
Eliminate the need for hiring expensive InfoSec professionals and costly ongoing training.
24/7 support to monitor alerts and proactively protect your environment.
Practitioners caring for your environment are always up-to-date on the latest threats.
Prevent usage abuse to free up bandwidth for legitimate business needs.
PROTECT YOUR NETWORK WITH PURPOSE-BUILT SOLUTIONS
- Endpoint Protection
- VPN
- Managed SOC
- Vulnerability Assessments
- Awareness Training
- Penetration Testing
- Web Content Filtering
- Email Security
- Compliance Audits
Curious to Know More?
Review our latest flyer to discover how Advantage will protect your enterprise against malicious activity with leading technology providers and solutions.COMMAND CENTER℠
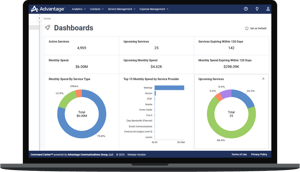
Our proprietary Command Center℠ SaaS platform offers a single view into every aspect of your global technology ecosystem from contract renewals to open support ticket tracking, and everything in between.
Bring better accuracy to your connectivity services data to drive more impactful decisions across your enterprise with this one resource.
Advantage FAQ:
Learn more about our organization and what makes our approach to technology lifecycle optimization unique by reviewing some of our most frequently asked questions, such as:We routinely save our customers 20-40% in service procurement costs in addition to shortening implementation timelines by nearly 25%. We offer a genuine return on investment from a true partner with real “skin in the game”.
Most clients say they love having Advantage as an extension of their team, providing expertise across the entire technology lifecycle, while reducing lifecycle operating expenses.
YOUR COMPETITIVE ADVANTAGE
Advisory and Design
Advantage brings more the 20 years of experience to your organization in designing scalable communications technology solutions across voice, data, cloud, and mobility.
.png?width=300&name=Website%20Provider%20Logos%20(3).png)
SUPERIOR ENTERPRISE CONNECTIVITY FROM 800+ GLOBAL PROVIDERS
Explore modern cybersecurity services powered by hundreds of the world's best carriers and managed by our experts.PRODUCT FEATURE TWO
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. Lorem ipsum dolor sit amet.

RELATED PROJECTS AND INSIGHTS
Explore more articles on the topic of cybersecurity to stay ahead of new trends and global activity.
Read MoreCyber attack examples and concerns that IT leaders should consider.
Read More.png?width=600&height=154&name=Advantage-Logo-Tagline-Color-Reversed%20(1).png)